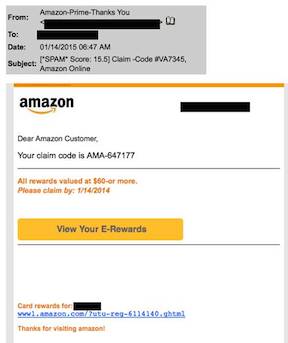
One technique of hackers is sending phony messages that masquerade as legitimate email, such as this one pretending to be from Amazon. The tactic, called phishing, is an attempt to lure users to click into a fake website or download harmful code.
The fields of animal health care and digital entertainment may be worlds apart, but it appears veterinarians and Sony employees have at least one thing in common: they sometimes choose abysmal passwords to protect their online accounts.
Think “password.”
These days, many would argue that a business without an online presence is doing itself a grave disservice. At the same time, being online is a risk, considering that reports of cyberattacks arrive in a seemingly constant stream.
Nearly half of adult Americans had accounts hacked in 2014, according to
CNN Money; Kmart and Staples are among the most recent to join the ranks of hacked retail giants such as Target and Home Depot.
“It’s not like getting struck by lightning,” said Lorrie Cranor, director of the Usable Privacy and Security Laboratory at Carnegie Mellon University. “It’s fairly common for people to have their accounts compromised.”
The veterinary world is no exception. eVetSites, a service of the Veterinary Information Network (VIN) that creates websites for veterinarians, sees hackers regularly invade users’ email accounts — a problem that is common among email service providers. (VIN is an online community for the profession and parent of the VIN News Service.)
Hank Haines, development manager of the software used by eVetSites, said it happens 10 to 20 times a year, largely thanks to weak passwords, passwords used across multiple sites and viruses.
Some may assume they have nothing to protect, but the consequences of hacking can extend far beyond the user to family and friends, developers who rush to do damage control and others on the same server.
That is why web developers and cybersecurity experts would be thrilled to see people add “step up Internet security” to their list of goals for 2015.
“An ounce of prevention is a ton of cure,” said Dr. Tony Bartels, a VIN employee who manages eVetSites. “Sometimes, it’s just bad luck, but if you take a few minutes to think about it … you can greatly reduce your risk.”
Make it harder on hackersWhen hackers recently stole heaps of data from Sony Pictures Entertainment, they got their hands on
thousands of usernames and passwords. On the list? “password” and “s0ny123.” At eVetSites, Bartels is compelled to look at users’ passwords after accounts are hacked. That list includes “123456” and “puppies.”
Weak, guessable passwords leave users vulnerable.
Once hackers have a username or an email address — 53 million were acquired in the recent Home Depot hack alone — they can use software to run through the dictionary, combing thousands of possible passwords and password variations in seconds.
Haines said he sees a spike in suspicious activity after large retail breaches and at the end of the year, when he believes hackers try out passwords acquired from one hack or start guessing passwords for their list of collected emails. Cyberattacks tend to surge during the holidays due to the increase in online traffic and transactions.
“There are layers of security in place to protect against this,” Bartels said. “We have spent a significant amount of time and money on this over the last couple of years. But without that ‘buy in’ at the end-user level, we are all always at risk.”
eVetSites administrators consistently encourage users to
strengthen their passwords. Adding an exclamation mark at the end of a password or a one at the beginning, however, won’t do the job.
“Don’t think you are being clever by changing the “o” to a zero,” said Eva Velasquez, director of the Identity Theft Resource Center, a nonprofit that assists victims of identity theft.
To create strong passwords, experts suggest these rules:
• Make passwords 8 to 12 characters long.
• Use a mix of uppercase and lowercase letters, numbers and special characters.
• Don’t use words that can be found in the dictionary.
Cranor suggested using a mnemonic device to help develop passwords: Think of a memorable sentence that is not a popular phrase, famous quote or song lyric, and string the first letters of each word together while mixing in numbers and symbols.
For example, “Walking my two Yorkshire terriers at the park keeps me stress-free,” might become: wm2YT@tpkmS_F.
Experts also warn not to use the same password for multiple sites, as it can make life much easier on a hacker who manages to crack one well-thought-out password.
If keeping track of dozens of complex passwords seems forbidding, Cranor has some easy advice.
“The simplest thing you can do is write them down,” she said. “It’s actually not a bad thing.”
She explained that when the main concern is malevolent strangers out in cyber land, physically writing passwords — on paper, not on a document on a computer — and storing them in a secure place can be a good option.
If a user is worried about family members, housemates or co-workers finding a secret stash of passwords, another option is a digital password manager — a program that helps users generate and keep track of complex passwords.
Virus protection also is high on the list of safe Internet practices. Security experts constantly play catch-up with new viruses, but without at least some kind of up-to-date virus protection software, Velasquez said, users could fall prey to something really old. And no, having a Mac does not make you invincible.
“Some systems have more robust programs in place,” Velasquez said, “but none of them are impenetrable. There’s no perfect infrastructure that can’t be breached.”
Velasquez also recommended strengthening privacy settings on social media to keep hackers from poking around for personal information such as birthdays, places lived and “likes” to help them access accounts or answer security questions.
“The reality is that the more info a crook has, the more they can socially engineer the rest of the puzzle,” she said.
Velasquez and Cranor echoed that a little common sense can go a long way. Users should be cautious about what they click on and download, and be wary of phishing — fake emails that look legitimate and entice the user into providing information, logging on to a fake website or downloading a harmful file.
At eVetsites, one of Haines' anti-hacking tasks involves catching spam being sent to or from eVetsites email accounts. “I spend a lot of time trying to track down what the spammer is using to send spam out and where on the Internet the email is being sent,” he said.
Email is portal to identity Cybersecurity experts attribute lackadaisical attitudes about Internet security to the belief that one is not a target, or that a particular account isn’t that important. But hackers aren’t necessarily looking for sensitive information from the get-go. Instead, they are probing for vulnerability.
“There’s making it easy and there’s making it hard,” Velasquez said. “They are looking for the low-hanging fruit.”
That low-hanging fruit can be a means to something greater: access to other accounts, a way into a network or system, or a host for sending malicious material to others.
Once attackers crack an email account, for example, they can mine messages for more sensitive information, reset passwords to other websites, or impersonate the user and send malware and viruses to the victim’s family and friends.
“I think people forget how truly valuable their email password is,” Velasquez said. “They go through all the trouble of making complex passwords for financial institutions and think ‘eh, email,’ when really, those are the keys to the kingdom.”
From Bartels’ perspective, when an eVetSites email account is hacked, everyone suffers. When several email accounts were compromised after Thanksgiving,
the breach temporarily slowed down the entire eVetSites email system.
Email servers use various factors to determine if other servers are safe, assigning them a “reputation.” When an eVetSites email account is hacked and used to send spam, it can lead to other servers temporarily refusing to accept email from eVetSites accounts overall.
“That means that if a single customer loses their password and our servers are used to send out spam, it affects all of our email customers,” Haines said. “This is a big responsibility and it is why we have to work to remedy the problem as quickly as possible.”
He added: “It’s definitely stressful. Pretty much everything we are working on comes to a complete halt and it’s all-hands-on-deck to ensure our ‘rep’ doesn’t take a big hit.”
Among its protections against hacking, eVetsites has systems that monitor the rate at which email is being sent from users. When the systems detect an uptick, the email systems are paused and eVetsite administrators are notified. This enables the technical team to clean out the spam, shut down the email of the hacked account and restart the flow of emails from the system before the intrusion does wide-ranging damage.
After the Thanksgiving event, eVetsites stepped up security further by monitoring the rate at which the systems deferred emails. “A high rate of ‘deferred’ emails is sometimes indicative of minor, everyday spam activity turning into a full-blown spam attack,” Bartels explained.
“We have to try to stay ahead of the hackers by continuing to add layers of protection on our end,” he said. “However, the last ‘gateway’ lies at the individual-user level.”
Owners of breached accounts are notified and guided through the process of updating virus protection and changing passwords before their accounts are re-enabled.
Cranor envisions a future where users no longer have to worry about cybersecurity, but until then, she said, it’s everyone’s responsibility.
“I’m surprised we can’t fix the problem for people — you don’t want to spend time doing security and I don’t think you should have to. But as of right now, you still do. It’s important that everyone participates.”